“Record Everything Now, Decrypt Later” Is Not Sci-Fi Anymore (But It’s Also Not “Game Over”)
Quantum computers won’t magically read every HTTPS session on Earth. But if you’re storing sensitive traffic today, you’re already making a bet about the next decade.
Forward secrecy protects you from stolen keys. It does not protect you from Shor. The good news: post-quantum TLS is already leaking into the real world. The bad news: most people are still “waiting for certainty.”
The dramatic claim everyone loves
“If a cryptographically relevant quantum computer shows up in ~10 years, then all HTTPS you record today can be decrypted later.”
It’s a fantastic sentence. Short. Terrifying. Gets engagement. Sells consulting.
It’s also slightly too dramatic.
The real version is less Hollywood and more… compliance spreadsheet:
A meaningful slice of recorded classical TLS traffic could become decryptable if large-scale fault-tolerant quantum computing arrives.
“All traffic” is overstated because (a) hybrid post-quantum key exchange is already rolling out in parts of the ecosystem, and (b) quantum decryption has throughput limits: with ECDHE you don’t crack “one key to rule them all”, you crack sessions.
So yes, the threat is real. No, it’s not a magic “decrypt the internet” button.
1. What has to break to read recorded HTTPS later
Modern HTTPS is basically:
Handshake (key exchange + authentication)
Symmetric crypto for the actual data (AES-GCM, ChaCha20-Poly1305)
The important bit:
Symmetric crypto isn’t “suddenly dead” because of quantum. Grover gives a speedup, but it doesn’t turn AES into wet cardboard overnight (and we can compensate by using appropriate key sizes).
The weak spot is the asymmetric key exchange. Shor’s algorithm is the nightmare fuel here: it targets RSA and ECC-style problems, which are exactly what classic TLS key exchange relies on.
So if an attacker records your TLS handshake transcripts today, and later gets a CRQC, they can try to reconstruct session keys from the recorded material.
That’s the whole “store now, decrypt later” logic.
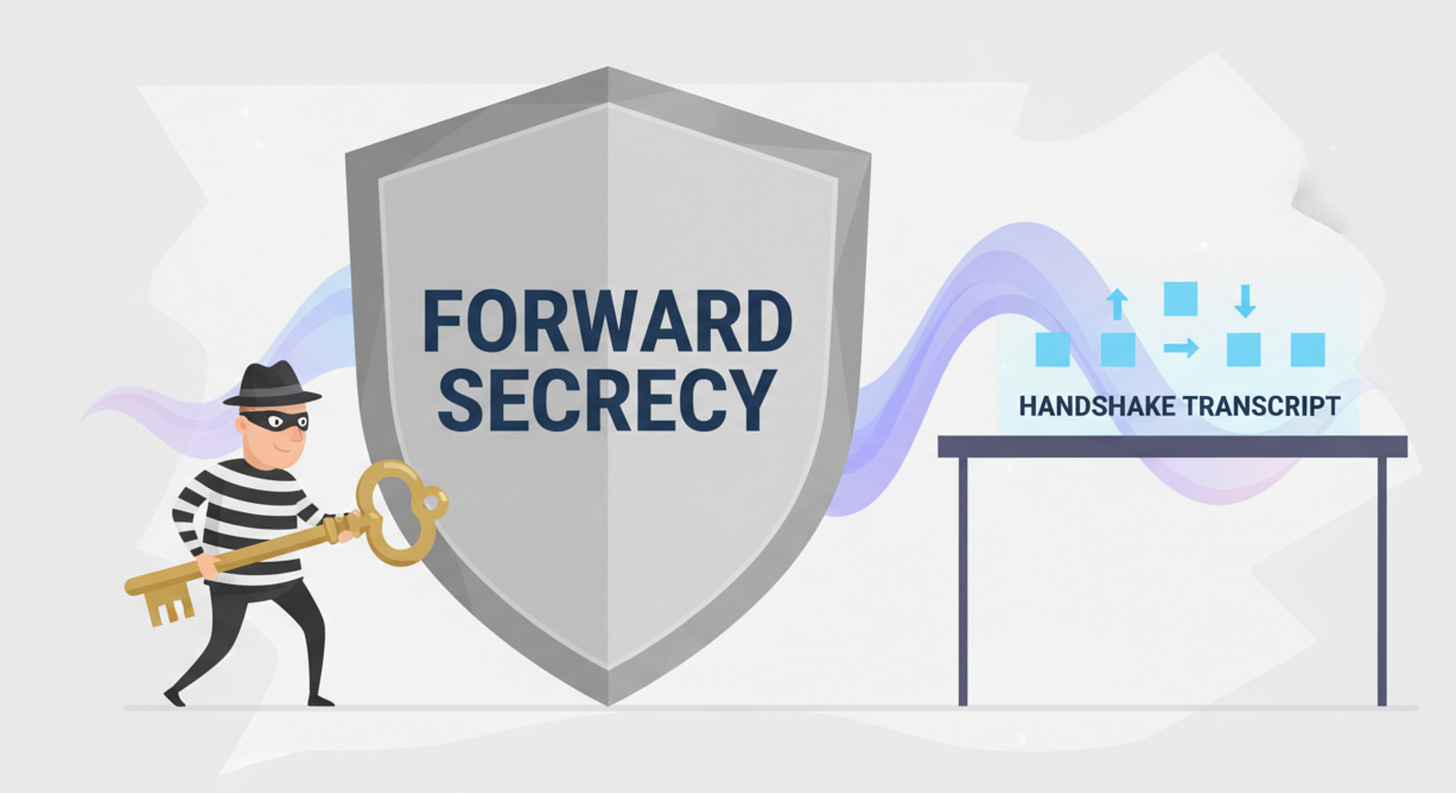
2. “But we have forward secrecy!”
Yes. And it’s brilliant.
Forward secrecy (ECDHE) saves you from the classic disaster scenario: “someone stole the server’s private key, now they can decrypt last year’s traffic.”
But against a CRQC?
Not so much.
With ECDHE, the handshake exposes enough public material that a sufficiently capable quantum attacker could solve the underlying ECC math and reconstruct the shared secret anyway. Which means: PFS doesn’t rescue recorded traffic from a quantum future.
So if your security strategy is “we use TLS 1.3, therefore we’re timeless,” I have bad news.
3. The part that already breaks the “ALL traffic” claim
Post-quantum isn’t just a PowerPoint now. The migration is messy, uneven, and absolutely happening.
NIST has published its first post-quantum crypto standards, including ML-KEM (the standardized Kyber line). That’s the sort of bureaucratic milestone that turns “research” into “procurement.”
Major players have been testing hybrid post-quantum key exchange for years, precisely to mitigate “store now, decrypt later” risk. Google previously ran PQ TLS experiments (CECPQ1/CECPQ2) as early as 2016–2018, explicitly framed around post-quantum confidentiality.
The TLS ecosystem has formalized hybrid approaches in drafts/spec work (classic + PQ combined so the exchange stays secure if either remains secure).
Cloudflare has also publicly worked on post-quantum / hybrid key agreement deployment and experimentation in TLS contexts.
Translation: some portion of traffic being generated “right now” is already starting to benefit from hybrid PQ key exchange, depending on client/server support and rollout strategy.
So “everything recorded today will be readable later” is already becoming wrong in practice — not because quantum is fake, but because migration has started.
4. “Okay, but how likely is the quantum part in 10 years?”
Here’s the honest answer: nobody knows, and anyone who pretends otherwise is selling something.
What we do have are public expert surveys and institutional timelines that scream the same message in different accents:
Expert panels disagree wildly, but they do not treat the risk as negligible. evolutionQ’s 2024 timeline material is a decent public anchor for “serious people are worried enough to plan.”
Governments are setting migration deadlines that assume you must move before you have certainty. (The subtext is always: “if you wait until the fire is visible, you will be standing in it.”)
And the resource estimates are still sobering. For RSA-2048, one well-known analysis discusses doing it in hours but at the cost of millions of noisy qubits with heavy error correction assumptions.
So: not guaranteed. Not impossible. Not something you want your long-term secrets to gamble on.
5. Why “decrypt everything” is also operationally dubious
Even if the CRQC shows up:
With ECDHE, you’re generally looking at per-session work. This isn’t “steal one master key, open all doors.” It’s more like: “pick doors you care about, and bring a very expensive lockpick to each one.”
Real adversaries triage. They won’t decrypt your archived lunch orders. They’ll decrypt:
state communications
high-value corporate traffic
anything with long shelf-life secrets (health data, biometrics, IP, legal strategy, dissident networks, etc.)
Also, plenty of high-value systems already add application-layer encryption on top of TLS. Even if TLS falls later, the contents may still be protected.
6. The practical takeaway: stop arguing about wording, start classifying data
If you want one rule that doesn’t require faith in quantum timelines:
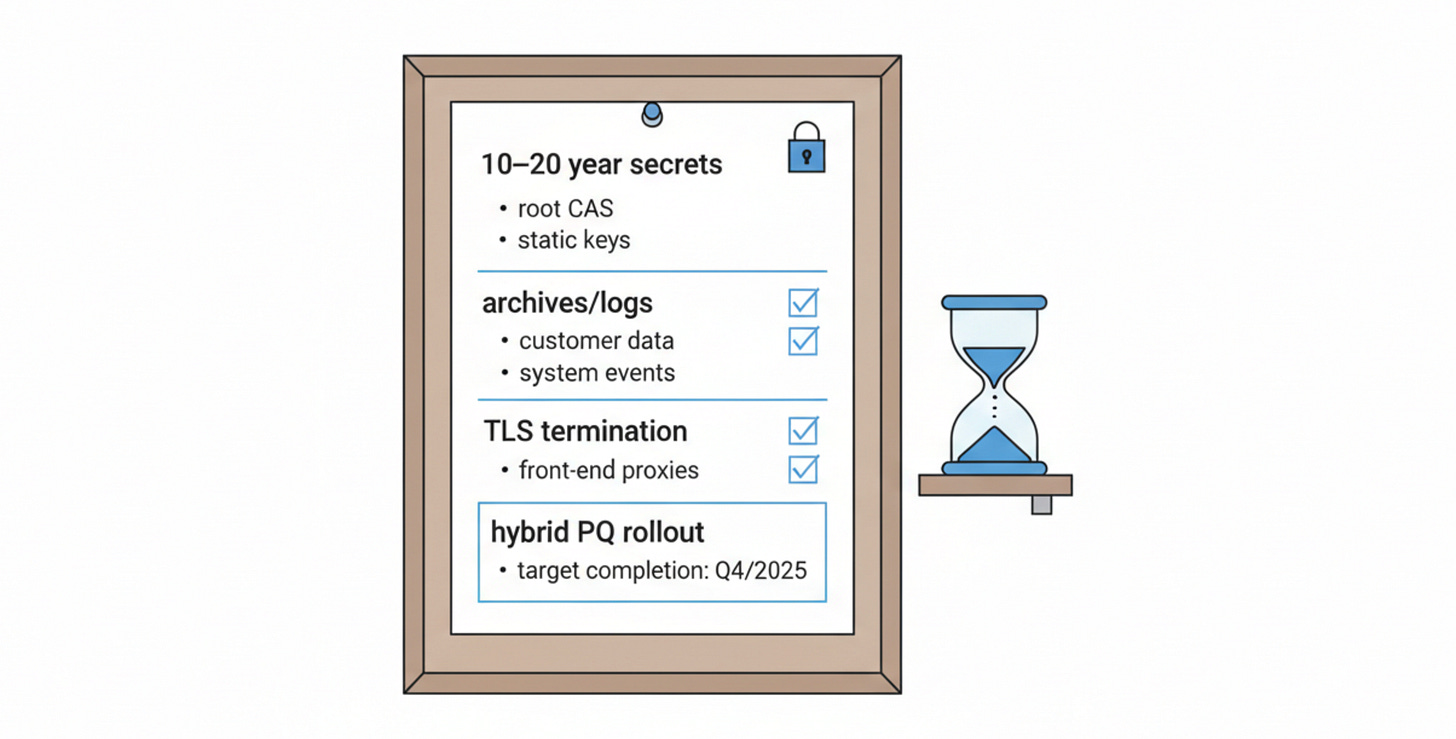
If the data must remain confidential for 10–20 years, treat today as “already under harvest.”
That’s it.
Not because quantum is inevitable next Tuesday. Because the cost of being wrong is asymmetric.
A simple action checklist
Inventory “long shelf-life” secrets (anything whose confidentiality matters beyond the typical product cycle).
Ask your providers (CDN, TLS termination, browsers/clients, VPNs):
Do you support hybrid PQ key exchange today?
Is it on by default anywhere?
What’s your migration plan?
Track standards-based PQC (NIST ML-KEM etc.) rather than bespoke crypto cosplay.
Prioritize upgrades where traffic is stored (logs, packet capture, compliance archives, “debug mode” dumps—yes, those too).
Closing thought: the future is annoying, not apocalyptic
Quantum risk is like buying insurance for a house that might be in a floodplain.
You don’t wait for the first wave to hit the sofa before googling “sandbags.”
You also don’t declare “ALL HOUSES WILL BE UNDERWATER” and run through the streets screaming.
You do the boring thing: classify what matters, upgrade the foundations, and quietly remove the obvious failure modes.
And then you let everyone else argue about the word “all” on the internet.




Great framing on the harvest now decrypt later threat. The per-session breakpoint for ECDHE is super important - people hear Shor and assume instant apocalypse. We started moving patient records to hybrid ML-KEM last quarter for exactly this reason. The asymmetric risk calc you laid out makes way more sense than waiting for consensus on timleines.